
| Cyber Security Management of IT and OT |
|
| IT support for the fleet performed with a single point of contact |
|
| IT maintenance of all the IT equipements onboard |
|
| Ensure cyber security compliance with supplier for OT perimeter |
|
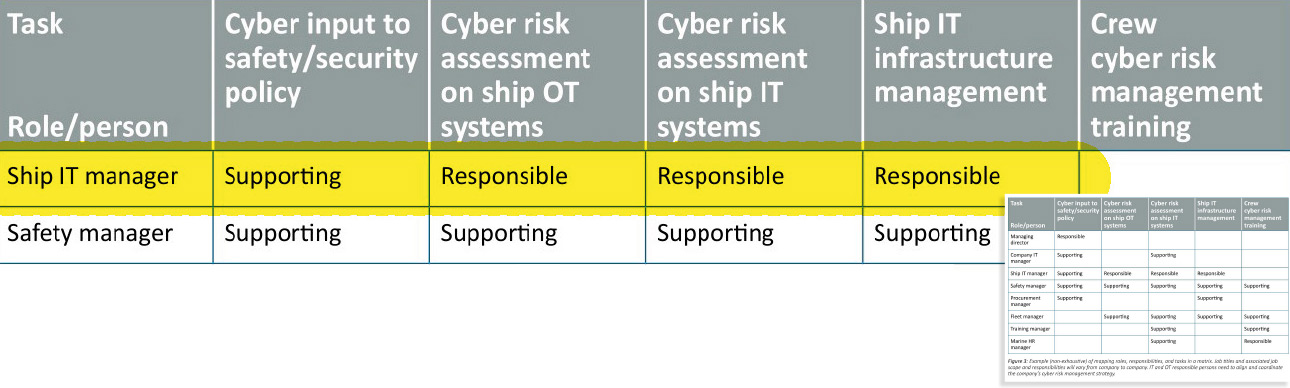
SHIP IT MANAGER role definition
This role has been defined by ISM and BIMCO
The latest revision of the cybersecurity guide onboard ships defines very concretely the role of ship IT manager: it is the one who manages and assesses IT and OT risks, and manages the ship's IT infrastructure. Our offer corresponds exactly to this scope and places us as your outsourced IT department.
Cybersecurity manager
Cybersecurity management on the IT and OT scope.
The management of cybersecurity is thought first, in a "Cyber Secure by design" approach.
It shapes all of our practices.
Find here the details of our cybersecurity management approach.
IT and OT Support
A single entry point to handle any IT issue onboard
A support service based on the ITIL reference standard serves as a single point of entry for crews and superintendents. It traces all requests in a dedicated tool, answer all questions and escalate them to suppliers when necessary. It gives advice, continuous training, is an event observer to detect cyber threats, and provides the crew with an essential resource to take ownership of the tools and manage incidents.
IT Maintenance.
Maintenance and system administration is performed in a normalized frame.
IT maintenance allows to guarantee the continuity of operation of tools and the preservation of cybersecurity. It is performed with a monitoring tool that can be integrated into your planned maintenance solution, and concerns both hardware and software. Management of access, state of health of the equipment, software updates, etc., everything is done and traceable in the maintenance history.

OT cyber compliance monitoring
The cybersecurity mastery of OT is done by monitoring the maintenance actions of the suppliers
OT suppliers perform contractual maintenance on their equipment, but the follow-up of interventions on the IT components of these OT must be conducted and traced. Establishment of work permits, monitoring of updates, control actions carried out by stakeholders, documentation of software version states, monitoring of backup and recovery tests of backups: we will complete the mastery of OT with you.